Cybersecurity
Discover certSIGN’s complete cybersecurity services dedicated to companies – from data security solutions to CSIRT services (Computer Security Incident Response Team).
Discover certSIGN’s complete cybersecurity services dedicated to companies – from data security solutions to CSIRT services (Computer Security Incident Response Team).
In the context of the continuous digitalization of companies’ activity, information cyber threats are increasing. certSIGN offers complete innovative solutions and services for companies that need protection of the information systems, covering both data security (enterprise security, desktop and mobile) and CSIRT services (security management services, proactive and reactive).
certSIGN cybersecurity services and solutions cover all scenarios for protecting digital assets from cyber threats, in accordance with applicable legislation and best practices in the field.
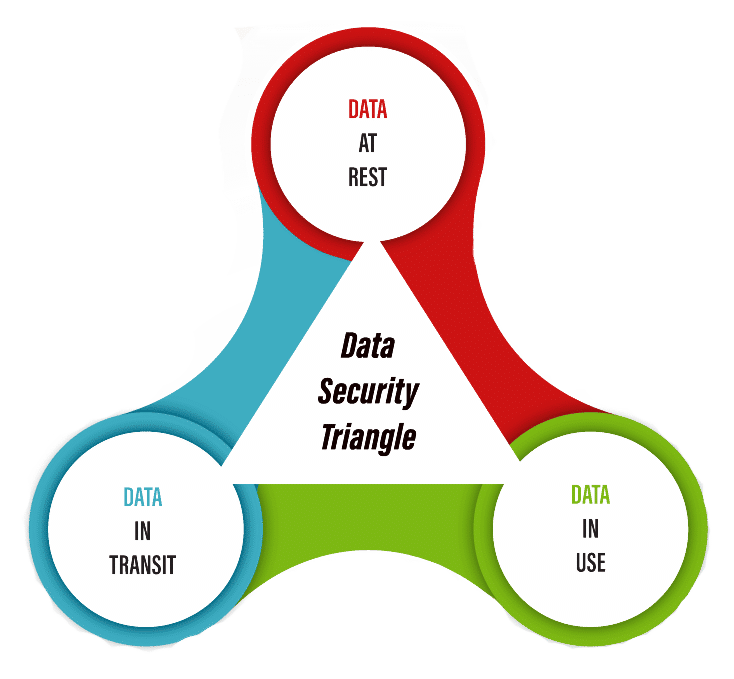
Data-centered security focuses on what must be secured and the appropriate data protection model, irrespective of where the data is located, if it is stored, used or in transit.
The defining feature of data-centered security is that the protection is applied to the data itself, through classification mechanisms, access control, secure encryption and, when necessary, secure deletion.

NIS Directive and Law 362/2018
certSIGN offers an extensive range of services that cover the information and system security requirements in compliance with the Law no. 362/2018 that translates the NIS Directive.

GDPR compliance
Although it can provide instruments that could punctually solve one or several of the GDPR provisions, certSIGN offers a comprehensive approach for maintaining permanent compliance.

#gomobile. Kandia testimonial
About the development and implementation of the customizable #gomobile Enterprise Mobility Management solution, which successfully integrates Samsung hardware and software components.
Send us your detailed request, and we will contact you to answer all your questions about our archiving solutions.

Details related to the electronic signature are available on the page with Answers to the most frequently asked questions of customers.
Quickly, useful information can be found about obtaining the confirmation document, costs, online purchase, video identification, renewal, installation and use:
When you receive the invoice, after purchasing a digital certificate for electronic signature
Numerous details are presented related to:
To use the certSIGN certificate for electronic signature in the Virtual Private Space (SPV) platform, we recommend following the instructions provided by ANAF for registration in the SPV.
To access the Virtual Private Space (VPS), the qualified certificate issued by certSIGN must be registered with the VPS by completing the requested information in the ANAF-SPV platform and uploading the requested documents, including the confirmation document countersigned by certSIGN at the address: https://www.anaf.ro/InregPersFizicePublic/#tabs-2 .
To obtain the confirmation document, follow one of these tutorials , depending on the type of signature you have:
The electronic signature is performed using a qualified digital certificate stored in the CLOUD, and to use the certificate in the CLOUD , the usage mechanism must first be configured.
After the video identification session has been accepted, the configurations prior to issuing the certificate can be performed, going through them in this order, stages:
Configure the signature authorization mechanism according to the instructions in the email “paperLESS : Configure authorization mechanism”:
Activate the cloud account according to the instructions in the “paperLESS email webSIGN : Account creation invitation”
Issuance of the certificate it is done when you first log in to your cloud account. On the page that opens Enter the authorization code generated by the application on your phone.
Placing an order to extend the validity of the certificate ensures: low costs, simple and fast process, 100% online, procedure under the exclusive control of the holder, retention of the current device (TOKEN) and retention of the PIN.
If the current certificate has expired, Renewal is no longer possible and a new electronic signature certificate must be purchased. We recommend accessing the certSIGN platform to purchase qualified TOKEN certificates and following the indicated steps.
certSIGN sends, to the email address in the certificate, the procedure for renewing the certificate 45 days before the expiration of the current certificate. If the procedure has not yet been followed, with 15 days before the certificate expires, certSIGN resends the renewal information email. Late submission of the request does not guarantee online renewal of the certificate.
Placing an order to extend the validity of the certificate ensures: low costs, simple and fast process, 100% online, procedure under the exclusive control of the holder, keeping the current webSIGN account and maintaining the authentication method.
The only condition that must be met for the online extension of the validity of the signature certificate (renewal) is that the current certificate must be within the validity period at the time of placing the extension order. The extension order is placed directly from the certSIGN websign.ro platform .
If the current certificate has expired, Renewal is no longer possible and a new certificate for electronic signature in CLOUD must be purchased. We recommend accessing the certSIGN platform for purchasing qualified certificates in the CLOUD and following the indicated steps.
certSIGN sends, to the email address in the certificate, the procedure for renewing the certificate 45 days before the expiration of the current certificate. If the procedure has not yet been followed, with 15 days before the certificate expires, certSIGN resends the renewal information email. Late submission of the application does not guarantee online renewal of the certificate.
webSIGN signing platform, during the 45 days before the expiration of the current certificate, a banner will be displayed with information regarding the deadline for certificate renewal. This banner will disappear after submitting the renewal request.
Log in to the websign.ro platform and renew the certificate in the CLOUD:
The certificate request generation stage is completed when the message “Request submitted for approval” is displayed in the cloud platform.
After validating the request, 3 days before the current certificate expires, certSIGN will automatically issue the new certificate. Regardless of the date the extension order is placed, the validity period of the new certificate will begin 3 days before the current certificate expires. After the new certificate is issued, the webSIGN platform can continue to be used for signing documents in the cloud , for the entire duration of the new validity period.
Placing an order to extend the validity of the certificate ensures: low costs, simple and fast process, 100% online, procedure under the exclusive control of the holder, keeping the current webSIGN account and maintaining the authentication method.
The only condition that must be met for the extension of the validity of the signature certificate (renewal) is that the current certificate must be within the validity period at the time of placing the extension order. The extension order is placed directly from the certSIGN websign.ro platform .
If the current certificate has expired, Renewal can no longer be made and a new certificate for electronic signature in CLOUD is required. We recommend accessing the certSIGN platform to purchase qualified certificates in CLOUD and following the indicated steps.
certSIGN sends, to the email address in the certificate, the procedure for renewing the certificate 45 days before the expiration of the current certificate. If the procedure has not yet been followed, with 15 days before the certificate expires, certSIGN resends the renewal information email. Late submission of the request does not guarantee online renewal of the certificate.
Placing an online order to extend the validity ensures: low costs, simple and fast process, 100% online, procedure under the exclusive control of the holder, retention of the current device (TOKEN) and retention of the PIN.
The only condition that must be met for the extension of the validity of the signature certificate (renewal) is that The current certificate must be within the validity period at the time of placing the extension order. Authentication is required in the certSIGN platform startrekey.certsign.ro, and authentication can only be done based on the current qualified certificate.
To the e-mail address in the certificate, certSIGN sends the procedure for renewing the certificate, 45 days before the current certificate expires. If the procedure has not yet been followed, 15 days before the certificate expires, certSIGN resends the renewal information e-mail.
Late submission of the application does not guarantee online renewal of the certificate.
the validity period has been exceeded , the current certificate can no longer be renewed and a new electronic signature certificate must be purchased. We recommend accessing certSIGN platform for the acquisition of qualified certificates on TOKEN and following the indicated steps.
The online certificate renewal procedure has three stages:
Regardless of the date the renewal order is placed, the validity period of the new certificate will begin 3 days before the current certificate expires. Please note that after renewal, it is NOT necessary to replace the current TOKEN. When uploading the new certificate to the TOKEN, the old certificate will be deleted.
It is necessary to redo enrollments/renewals in the platforms of the institutions where you will use the new certificate , such as: ANAF, CNAS, UNNPR, etc.
Check what solution exists if you are in one of the situations encountered by other customers regarding obtaining the confirmation document.
We remind you, the document is obtained simply and quickly. from the certSIGN confirmation platform. Repeat it as many times as necessary. You only need your qualified digital certificate for electronic signature.
The acquisition of the certSIGN Kit for electronic signature from the SICAP catalog can be done by following the steps in this order :
If the holder cannot appear in person at a certSIGN partner, the documents can be sent by courier/post to the certSIGN headquarters. The documents must be accompanied by the “Affidavit” authenticated by a notary or certified by a lawyer.
certSIGN headquarters address: Tudor Vladimirescu Boulevard, no. 29A, Sector 5, Bucharest, AFI TECH PARK 1 building, 2nd floor.
The tax invoice will be sent after the certificate is issued and will have a 30-day payment deadline.
In the SICAP catalog, the products are found as follows:
The acquisition of the certSIGN certificate in CLOUD for electronic signature from the SICAP catalog can be done by following the steps in this order :
If the holder cannot appear in person at a certSIGN partner, the documents can be sent by courier/post to the certSIGN headquarters. The documents must be accompanied by the “Affidavit” authenticated by a notary or certified by a lawyer.
certSIGN headquarters address: Tudor Vladimirescu Boulevard, no. 29A, Sector 5, Bucharest, AFI TECH PARK 1 building, 2nd floor.
The digital certificate will be issued automatically upon first entering an authorization code, after authenticating in the cloud platform account. paperLESS webSIGN .
The tax invoice will be sent after the certificate is issued and will have a 30-day payment deadline.
In the SICAP catalog, the products are found as follows:
The electronic signature is made using the qualified digital certificate stored on the TOKEN and, to use the certificate, the token management application must be installed on the computer.
So, if this is the first time you use the TOKEN on this computer:
The PIN code is transmitted using one of two options:
OR
The electronic signature is performed using a qualified digital certificate stored in the CLOUD, and to use the certificate in the CLOUD, the usage mechanism must first be configured.
After the video identification session has been accepted, the configurations prior to issuing the certificate can be performed, going through the steps in this order:
Configure the signature authorization mechanism according to the instructions in the email “paperLESS : Configure authorization mechanism”:
Activate the cloud account according to the instructions in the “paperLESS email webSIGN : Account creation invitation”
The certificate is issued upon first login to the cloud account . In the opened page, enter the authorization code generated by the application on the phone.
Unassisted video identification is an important element in the process of obtaining a qualified digital certificate for electronic signature. Issuance is possible only after identifying the holder of the qualified digital certificate, based on the identity document.
After completion, the video identification session must be validated by certSIGN. Our response will be sent within 24 hours, by email. If the session:
Watch this video that presents the conditions that must be respected during video identification .
We remind you that, to perform video identification, the following are necessary:
* The list of accepted identity documents for video identification is available HERE .
In this area, certSIGN provides services such as:
Products and services
We are best known for our electronic signature services, but our expertise covers areas such as digital identity, organizational and work device security, and archiving.
Research and innovation
At certSIGN, we align the theoretical aspects of technology with the needs of society, through national and European research programs and, at the same time, through private investment programs.
Read more details or send us a message.
In the field of archiving, certSIGN offers services such as: archival processing, document digitization, restoration, document storage, issuance of certificates, selection work, confidential destruction of information, processing and storage of electronic documents.
certSIGN’s cybersecurity services and solutions cover scenarios for protecting digital assets from cyber threats, in accordance with current legislative regulations and best practices in the field.
Find out details about:
Details on how to personalize the signature so that its appearance includes the information required by GEO 140/2020 regarding specialists in the fields of construction, architecture and urban planning are available on the Create signature appearance GEO 140/2020 page.
To purchase a qualified certificate from certSIGN for the electronic signing of documents in the fields of construction, architecture and urban planning, in accordance with GEO 140, these steps must be followed:
If the information related to the certificate holder is correct and complete, certSIGN will send the envelope with the Electronic Signature Kit to the postal address filled in the registration application. The envelope will contain:
PIN/PUK codes are generated electronically using an automated mechanism: the certificate holder receives and accesses a link and, on the opened page, fills in the requested information and the generation code received in the envelope. The resulting PIN.pdf file must be saved or printed. It will be required for the following uses of the TOKEN.
To access the Integrated Customs Information System (SIIV) to the AES and NCTS5 RO UMG Trader Produccione sections you must upload your qualified certificate and the intermediate certificate of the authority that issued the certificate. The certificates are uploaded to the UMG Trader platform , in one of the .cer/.der / .crt formats.
OBTAINING THE INTERMEDIATE CERTIFICATE:
OBTAINING THE PERSONAL CERTIFICATE:
On the web page Using the electronic signature certificate in the Integrated Customs Information System platform, more details are available about downloading the certificate of the holder and the certificate of the intermediate authority requested when registering for the submission of customs declarations using the electronic signature.
If the video identification session was interrupted, for any reason, or could not be validated, certSIGN will send by email, within a maximum of 24 hours, the necessary instructions for resuming and/or completing the identification process. It will not be necessary to rescind the payment. The conditions that must be met for identification are the same.
Wait for the new video identification link to be received and then resume the procedure. Pay close attention to the conditions that must be met during identification.
Watch this video that presents the conditions that must be respected during video identification .
We remind you that, to perform video identification, the following are necessary:
* The list of accepted identity documents for video identification is available HERE .
After completion, the video identification session must be validated by certSIGN. Our response will be sent within 24 hours, by email. If the session:
certSIGN transmits the PIN/PUK codes for certificates on TOKEN, using one of two options:
PIN/PUK TRANSMISSION IS DONE
ELECTRONIC if the email address associated with the digital certificate was validated after completing the certificate purchase request.
The document containing the PIN/PUK must be generated electronically by the certificate holder. This document can only be obtained after receiving the generation code. Access the link sent by certSIGN via email and, on the opened page, fill in the requested information and the generation code.
ATTENTION: After 3 unsuccessful attempts to generate PIN/PUK, the link is blocked. This situation must be reported to certSIGN.
Once completed, the document ( PIN.pdf ) containing the PIN/PUK must be saved and kept safe.
OR
PHYSICALLY – secure document, in an envelope, sent by courier to the postal address declared at the time of purchase, if the email address associated with the qualified digital certificate for the electronic signature was NOT validated after completing the certificate purchase request.
The confirmation document is obtained simply and quickly from the certSIGN platform . Whenever and as many times as necessary . You only need your qualified digital certificate for electronic signature.
You download the pre-filled document with your data. You sign it electronically. You send the signed document to be automatically countersigned by certSIGN. You receive the confirmation document signed by certSIGN. All actions in the same platform.
In detail, to obtain the confirmation document you must complete the following steps, in this order :
Follow one of these tutorials , depending on the type of signature you have:
he electronic signature is made using a qualified digital certificate, and to purchase a certificate stored in the CLOUD, the following steps must be followed:
If the information related to the certificate holder is correct and complete, certSIGN will send two invitations to the email address indicated in the registration form :
The right to use the electronic signature in the cloud will be granted only after configuring the authorization mechanism and activating the user account in the paperLESS signing platform webSIGN , according to the instructions received.
The digital certificate is issued automatically after logging into the cloud platform account. webSIGN , upon first entering an authorization code.
The electronic signature is made using a qualified digital certificate, and to purchase a certificate stored on TOKEN, the following steps must be followed:
If the information related to the certificate holder is correct and complete, certSIGN will send the envelope with the Electronic Signature Kit to the postal address indicated in the registration form. The envelope will contain :
The PIN/PUK codes will be delivered independently of the envelope containing the TOKEN . The delivery of the document containing the codes can be done:
For more information, you can also visit the Electronic signature with token page .
Didn’t find what you were looking for? Describe the situation you need an answer for in as much detail as possible.
Central Office:
29 A Tudor Vladimirescu Blvd, AFI Tech Park 1, District 5,
Bucharest, Romania, 050881
Social headquarters:
107A Oltenitei Avenue, District 4,
Bucharest, Romania
European Unique Identifier (EUID):
ROONRC.J2006000484402
Order No. Trade Register:
J2006000484402
Tax registration code:
RO18288250
Useful
Policies and procedures
Central Office:
29 A Tudor Vladimirescu Blvd, AFI Tech Park 1, S5, Bucharest, Romania
Social headquarters:
107A Oltenitei Avenue, S4,
Bucharest, Romania
European Unique Identifier (EUID): ROONRC.J2006000484402
Order No. Trade Register:
J2006000484402
Tax registration code:
RO18288250
Needing more informations?
Citește recomandările noastre legate de subiectul selectat. Dacă nu ai găsit ce căutai, solicită informații suplimentare.

Details related to the electronic signature are available on the page with Answers to the most frequently asked questions of customers.
Quickly, useful information can be found about obtaining the confirmation document, costs, online purchase, video identification, renewal, installation and use:
When you receive the invoice, after purchasing a digital certificate for electronic signature
Numerous details are presented related to:
To use the certSIGN certificate for electronic signature in the Virtual Private Space (SPV) platform, we recommend following the instructions provided by ANAF for registration in the SPV.
To access the Virtual Private Space (VPS), the qualified certificate issued by certSIGN must be registered with the VPS by completing the requested information in the ANAF-SPV platform and uploading the requested documents, including the confirmation document countersigned by certSIGN at the address: https://www.anaf.ro/InregPersFizicePublic/#tabs-2 .
To obtain the confirmation document, follow one of these tutorials , depending on the type of signature you have:
The electronic signature is performed using a qualified digital certificate stored in the CLOUD, and to use the certificate in the CLOUD , the usage mechanism must first be configured.
After the video identification session has been accepted, the configurations prior to issuing the certificate can be performed, going through them in this order, stages:
Configure the signature authorization mechanism according to the instructions in the email “paperLESS : Configure authorization mechanism”:
Activate the cloud account according to the instructions in the “paperLESS email webSIGN : Account creation invitation”
Issuance of the certificate it is done when you first log in to your cloud account. On the page that opens Enter the authorization code generated by the application on your phone.
Placing an order to extend the validity of the certificate ensures: low costs, simple and fast process, 100% online, procedure under the exclusive control of the holder, retention of the current device (TOKEN) and retention of the PIN.
If the current certificate has expired, Renewal is no longer possible and a new electronic signature certificate must be purchased. We recommend accessing the certSIGN platform to purchase qualified TOKEN certificates and following the indicated steps.
certSIGN sends, to the email address in the certificate, the procedure for renewing the certificate 45 days before the expiration of the current certificate. If the procedure has not yet been followed, with 15 days before the certificate expires, certSIGN resends the renewal information email. Late submission of the request does not guarantee online renewal of the certificate.
Placing an order to extend the validity of the certificate ensures: low costs, simple and fast process, 100% online, procedure under the exclusive control of the holder, keeping the current webSIGN account and maintaining the authentication method.
The only condition that must be met for the online extension of the validity of the signature certificate (renewal) is that the current certificate must be within the validity period at the time of placing the extension order. The extension order is placed directly from the certSIGN websign.ro platform .
If the current certificate has expired, Renewal is no longer possible and a new certificate for electronic signature in CLOUD must be purchased. We recommend accessing the certSIGN platform for purchasing qualified certificates in the CLOUD and following the indicated steps.
certSIGN sends, to the email address in the certificate, the procedure for renewing the certificate 45 days before the expiration of the current certificate. If the procedure has not yet been followed, with 15 days before the certificate expires, certSIGN resends the renewal information email. Late submission of the application does not guarantee online renewal of the certificate.
webSIGN signing platform, during the 45 days before the expiration of the current certificate, a banner will be displayed with information regarding the deadline for certificate renewal. This banner will disappear after submitting the renewal request.
Log in to the websign.ro platform and renew the certificate in the CLOUD:
The certificate request generation stage is completed when the message “Request submitted for approval” is displayed in the cloud platform.
After validating the request, 3 days before the current certificate expires, certSIGN will automatically issue the new certificate. Regardless of the date the extension order is placed, the validity period of the new certificate will begin 3 days before the current certificate expires. After the new certificate is issued, the webSIGN platform can continue to be used for signing documents in the cloud , for the entire duration of the new validity period.
Placing an order to extend the validity of the certificate ensures: low costs, simple and fast process, 100% online, procedure under the exclusive control of the holder, keeping the current webSIGN account and maintaining the authentication method.
The only condition that must be met for the extension of the validity of the signature certificate (renewal) is that the current certificate must be within the validity period at the time of placing the extension order. The extension order is placed directly from the certSIGN websign.ro platform .
If the current certificate has expired, Renewal can no longer be made and a new certificate for electronic signature in CLOUD is required. We recommend accessing the certSIGN platform to purchase qualified certificates in CLOUD and following the indicated steps.
certSIGN sends, to the email address in the certificate, the procedure for renewing the certificate 45 days before the expiration of the current certificate. If the procedure has not yet been followed, with 15 days before the certificate expires, certSIGN resends the renewal information email. Late submission of the request does not guarantee online renewal of the certificate.
Placing an online order to extend the validity ensures: low costs, simple and fast process, 100% online, procedure under the exclusive control of the holder, retention of the current device (TOKEN) and retention of the PIN.
The only condition that must be met for the extension of the validity of the signature certificate (renewal) is that The current certificate must be within the validity period at the time of placing the extension order. Authentication is required in the certSIGN platform startrekey.certsign.ro, and authentication can only be done based on the current qualified certificate.
To the e-mail address in the certificate, certSIGN sends the procedure for renewing the certificate, 45 days before the current certificate expires. If the procedure has not yet been followed, 15 days before the certificate expires, certSIGN resends the renewal information e-mail.
Late submission of the application does not guarantee online renewal of the certificate.
the validity period has been exceeded , the current certificate can no longer be renewed and a new electronic signature certificate must be purchased. We recommend accessing certSIGN platform for the acquisition of qualified certificates on TOKEN and following the indicated steps.
The online certificate renewal procedure has three stages:
Regardless of the date the renewal order is placed, the validity period of the new certificate will begin 3 days before the current certificate expires. Please note that after renewal, it is NOT necessary to replace the current TOKEN. When uploading the new certificate to the TOKEN, the old certificate will be deleted.
It is necessary to redo enrollments/renewals in the platforms of the institutions where you will use the new certificate , such as: ANAF, CNAS, UNNPR, etc.
Check what solution exists if you are in one of the situations encountered by other customers regarding obtaining the confirmation document.
We remind you, the document is obtained simply and quickly. from the certSIGN confirmation platform. Repeat it as many times as necessary. You only need your qualified digital certificate for electronic signature.
The acquisition of the certSIGN Kit for electronic signature from the SICAP catalog can be done by following the steps in this order :
If the holder cannot appear in person at a certSIGN partner, the documents can be sent by courier/post to the certSIGN headquarters. The documents must be accompanied by the “Affidavit” authenticated by a notary or certified by a lawyer.
certSIGN headquarters address: Tudor Vladimirescu Boulevard, no. 29A, Sector 5, Bucharest, AFI TECH PARK 1 building, 2nd floor.
The tax invoice will be sent after the certificate is issued and will have a 30-day payment deadline.
In the SICAP catalog, the products are found as follows:
The acquisition of the certSIGN certificate in CLOUD for electronic signature from the SICAP catalog can be done by following the steps in this order :
If the holder cannot appear in person at a certSIGN partner, the documents can be sent by courier/post to the certSIGN headquarters. The documents must be accompanied by the “Affidavit” authenticated by a notary or certified by a lawyer.
certSIGN headquarters address: Tudor Vladimirescu Boulevard, no. 29A, Sector 5, Bucharest, AFI TECH PARK 1 building, 2nd floor.
The digital certificate will be issued automatically upon first entering an authorization code, after authenticating in the cloud platform account. paperLESS webSIGN .
The tax invoice will be sent after the certificate is issued and will have a 30-day payment deadline.
In the SICAP catalog, the products are found as follows:
The electronic signature is made using the qualified digital certificate stored on the TOKEN and, to use the certificate, the token management application must be installed on the computer.
So, if this is the first time you use the TOKEN on this computer:
The PIN code is transmitted using one of two options:
OR
The electronic signature is performed using a qualified digital certificate stored in the CLOUD, and to use the certificate in the CLOUD, the usage mechanism must first be configured.
After the video identification session has been accepted, the configurations prior to issuing the certificate can be performed, going through the steps in this order:
Configure the signature authorization mechanism according to the instructions in the email “paperLESS : Configure authorization mechanism”:
Activate the cloud account according to the instructions in the “paperLESS email webSIGN : Account creation invitation”
The certificate is issued upon first login to the cloud account . In the opened page, enter the authorization code generated by the application on the phone.
Unassisted video identification is an important element in the process of obtaining a qualified digital certificate for electronic signature. Issuance is possible only after identifying the holder of the qualified digital certificate, based on the identity document.
After completion, the video identification session must be validated by certSIGN. Our response will be sent within 24 hours, by email. If the session:
Watch this video that presents the conditions that must be respected during video identification .
We remind you that, to perform video identification, the following are necessary:
* The list of accepted identity documents for video identification is available HERE .
In this area, certSIGN provides services such as:
Products and services
We are best known for our electronic signature services, but our expertise covers areas such as digital identity, organizational and work device security, and archiving.
Research and innovation
At certSIGN, we align the theoretical aspects of technology with the needs of society, through national and European research programs and, at the same time, through private investment programs.
Read more details or send us a message.
In the field of archiving, certSIGN offers services such as: archival processing, document digitization, restoration, document storage, issuance of certificates, selection work, confidential destruction of information, processing and storage of electronic documents.
certSIGN’s cybersecurity services and solutions cover scenarios for protecting digital assets from cyber threats, in accordance with current legislative regulations and best practices in the field.
Find out details about:
Details on how to personalize the signature so that its appearance includes the information required by GEO 140/2020 regarding specialists in the fields of construction, architecture and urban planning are available on the Create signature appearance GEO 140/2020 page.
To purchase a qualified certificate from certSIGN for the electronic signing of documents in the fields of construction, architecture and urban planning, in accordance with GEO 140, these steps must be followed:
If the information related to the certificate holder is correct and complete, certSIGN will send the envelope with the Electronic Signature Kit to the postal address filled in the registration application. The envelope will contain:
PIN/PUK codes are generated electronically using an automated mechanism: the certificate holder receives and accesses a link and, on the opened page, fills in the requested information and the generation code received in the envelope. The resulting PIN.pdf file must be saved or printed. It will be required for the following uses of the TOKEN.
To access the Integrated Customs Information System (SIIV) to the AES and NCTS5 RO UMG Trader Produccione sections you must upload your qualified certificate and the intermediate certificate of the authority that issued the certificate. The certificates are uploaded to the UMG Trader platform , in one of the .cer/.der / .crt formats.
OBTAINING THE INTERMEDIATE CERTIFICATE:
OBTAINING THE PERSONAL CERTIFICATE:
On the web page Using the electronic signature certificate in the Integrated Customs Information System platform, more details are available about downloading the certificate of the holder and the certificate of the intermediate authority requested when registering for the submission of customs declarations using the electronic signature.
If the video identification session was interrupted, for any reason, or could not be validated, certSIGN will send by email, within a maximum of 24 hours, the necessary instructions for resuming and/or completing the identification process. It will not be necessary to rescind the payment. The conditions that must be met for identification are the same.
Wait for the new video identification link to be received and then resume the procedure. Pay close attention to the conditions that must be met during identification.
Watch this video that presents the conditions that must be respected during video identification .
We remind you that, to perform video identification, the following are necessary:
* The list of accepted identity documents for video identification is available HERE .
After completion, the video identification session must be validated by certSIGN. Our response will be sent within 24 hours, by email. If the session:
certSIGN transmits the PIN/PUK codes for certificates on TOKEN, using one of two options:
PIN/PUK TRANSMISSION IS DONE
ELECTRONIC if the email address associated with the digital certificate was validated after completing the certificate purchase request.
The document containing the PIN/PUK must be generated electronically by the certificate holder. This document can only be obtained after receiving the generation code. Access the link sent by certSIGN via email and, on the opened page, fill in the requested information and the generation code.
ATTENTION: After 3 unsuccessful attempts to generate PIN/PUK, the link is blocked. This situation must be reported to certSIGN.
Once completed, the document ( PIN.pdf ) containing the PIN/PUK must be saved and kept safe.
OR
PHYSICALLY – secure document, in an envelope, sent by courier to the postal address declared at the time of purchase, if the email address associated with the qualified digital certificate for the electronic signature was NOT validated after completing the certificate purchase request.
The confirmation document is obtained simply and quickly from the certSIGN platform . Whenever and as many times as necessary . You only need your qualified digital certificate for electronic signature.
You download the pre-filled document with your data. You sign it electronically. You send the signed document to be automatically countersigned by certSIGN. You receive the confirmation document signed by certSIGN. All actions in the same platform.
In detail, to obtain the confirmation document you must complete the following steps, in this order :
Follow one of these tutorials , depending on the type of signature you have:
he electronic signature is made using a qualified digital certificate, and to purchase a certificate stored in the CLOUD, the following steps must be followed:
If the information related to the certificate holder is correct and complete, certSIGN will send two invitations to the email address indicated in the registration form :
The right to use the electronic signature in the cloud will be granted only after configuring the authorization mechanism and activating the user account in the paperLESS signing platform webSIGN , according to the instructions received.
The digital certificate is issued automatically after logging into the cloud platform account. webSIGN , upon first entering an authorization code.
The electronic signature is made using a qualified digital certificate, and to purchase a certificate stored on TOKEN, the following steps must be followed:
If the information related to the certificate holder is correct and complete, certSIGN will send the envelope with the Electronic Signature Kit to the postal address indicated in the registration form. The envelope will contain :
The PIN/PUK codes will be delivered independently of the envelope containing the TOKEN . The delivery of the document containing the codes can be done:
For more information, you can also visit the Electronic signature with token page .
Didn’t find what you were looking for? Describe the situation you need an answer for in as much detail as possible.
Ai nevoie de mai multe informații?
Citește recomandările noastre legate de subiectul selectat. Dacă nu ai găsit ce căutai, solicită informații suplimentare.

Detalii legate de semnătura electronică sunt disponibile pe pagina cu Răspunsurile pentru cele mai frecvente întrebări ale clienților.
Rapid, pot fi aflate informații utile despre obținerea documentului de confirmare, costuri, achiziție online, identificare video, reînnoire, instalare și utilizare:
Sunt prezentate numeroase detalii legate de :
Semnătura electronică se realizează cu ajutorul unui certificat digital calificat stocat în CLOUD, iar pentru utilizarea certificatului din CLOUD trebuie configurat mecanismul de utilizare, mai întâi.
Dupa ce sesiunea de identificare video a fost acceptată pot fi realizate configurările premergătoare emiterii certificatului, parcurgând în această ordine, etapele:
Configurarea mecanismului de autorizare a semnăturilor conform indicațiilor din emailul “paperLESS: Configurare mecanism de autorizare”:
Activarea contului de cloud conform indicațiilor din emailul “paperLESS webSIGN: Invitație creare cont”
Emiterea certificatului se face la prima autentificare în contul de cloud. În pagina deschisă se introduce codul de autorizare generat de aplicația de pe telefon.
Plasarea comenzii pentru prelungirea valabilității certificatului are numeroase beneficii: costuri reduse, proces simplu și rapid, 100% online, procedură aflată exclusiv în controlul titularului, păstrarea dispozitivului (TOKEN-ului) actual și păstrarea PIN-ului.
Dacă certificatul actual a expirat, nu mai poate fi făcută reînnoirea și este necesară achiziția unui nou certificat pentru semnătură electronică. Recomandăm accesarea platformei certSIGN pentru achiziția certificatelor calificate pe TOKEN și urmarea pașilor indicați.
certSIGN transmite, pe adresa de e-mail din certificat, procedura pentru reînnoirea certificatului cu 45 de zile înainte de expirarea certificatului actual. Dacă procedura nu a fost încă urmată, cu 15 zile înainte de expirarea certificatului, certSIGN retrimite e-mail-ul de informare privind reînnoirea. Transmiterea întârziată a cererii nu garantează reînnoirea online certificatului.
Plasarea comenzii pentru prelungirea valabilității certificatului are numeroase beneficii: costuri reduse, proces simplu și rapid, 100% online, procedură aflată exclusiv în controlul titularului, păstrarea contului webSIGN actual și păstrarea modalității de autentificare.
Dacă certificatul actual a expirat, nu mai poate fi făcută reînnoirea și este necesară achiziția unui nou certificat pentru semnătură electronică în CLOUD. Recomandăm accesarea platformei certSIGN pentru achiziția certificatelor calificate în CLOUD și urmarea pașilor indicați.
certSIGN transmite, pe adresa de e-mail din certificat, procedura pentru reînnoirea certificatului cu 45 de zile înainte de expirarea certificatului actual. Dacă procedura nu a fost încă urmată, cu 15 zile înainte de expirarea certificatului, certSIGN retrimite e-mail-ul de informare privind reînnoirea. Transmiterea întârziată a cererii nu garantează reînnoirea online a certificatului.
În platforma de semnare webSIGN, pe perioada celor 45 de zile înainte de expirarea certificatului actual, va afișat un banner cu informarea privind termenul pentru reînnoirea certificatului.
Pașii care trebuie urmați pentru reînnoirea certificatului în CLOUD:
Etapa de generarea a cererii de certificat este finalizată când în platforma de cloud este afișat mesajul “Cererea a fost trimisă pentru aprobare”.
După validarea cererii, cu 3 zile înainte de expirarea certificatului actual, certSIGN va emite automat noul certificat. Indiferent de data la care este făcută comanda pentru prelungire, perioada de valabilitate a noului certificatului va începe cu 3 zile înainte de expirarea actualului certificat. După emiterea noului certificat, platforma webSIGN va putea fi utilizată în continuare pentru semnarea documentelor în cloud, pe toată durata noii perioade de valabilitate.
Plasarea comenzii pentru prelungirea valabilității certificatului are numeroase beneficii: costuri reduse, proces simplu și rapid, 100% online, procedură aflată exclusiv în controlul titularului, păstrarea contului webSIGN actual și păstrarea modalității de autentificare.
Dacă certificatul actual a expirat, nu mai poate fi făcută reînnoirea și este necesară achiziția unui nou certificat pentru semnătură electronică în CLOUD. Recomandăm accesarea platformei certSIGN pentru achiziția certificatelor calificate în CLOUD și urmarea pașilor indicați.
certSIGN transmite, pe adresa de e-mail din certificat, procedura pentru reînnoirea certificatului cu 45 de zile înainte de expirarea certificatului actual. Dacă procedura nu a fost încă urmată, cu 15 zile înainte de expirarea certificatului, certSIGN retrimite e-mail-ul de informare privind reînnoirea. Transmiterea întârziată a cererii nu garantează reînnoirea online a certificatului.
Plasarea comenzii online pentru prelungirea valabilității certificatului are numeroase beneficii: costuri reduse, proces simplu și rapid, 100% online, procedură aflată exclusiv în controlul titularului, păstrarea dispozitivului (TOKEN-ului) actual și păstrarea PIN-ului.
Pe adresa de e-mail din certificat, certSIGN transmite procedura pentru reînnoirea certificatului, cu 45 de zile înainte de expirarea certificatului actual. Dacă procedura nu a fost încă urmată, cu 15 zile înainte de expirarea certificatului, certSIGN retrimite e-mail-ul de informare privind reînnoirea.
Transmiterea întârziată a cererii nu garantează reînnoirea online a certificatului.
Dacă a fost depășită perioada de valabilitate, certificatul actual nu mai poate fi reînnoit și este necesară achiziția unui nou certificat pentru semnătură electronică. Recomandăm accesarea platformei certSIGN pentru achiziția certificatelor calificate pe TOKEN și urmarea pașilor indicați.
Procedura de reînnoire online a certificatului are trei etape:
Indiferent de data la care este făcută comanda pentru prelungire, perioada de valabilitate a noului certificatului va începe cu 3 zile înainte de expirarea actualului certificat. Reamintim, după reînnoire NU este necesară înlocuirea TOKEN-ului actual. La încărcarea pe TOKEN a noului certificat, vechiul certificat va fi șters.
Este necesar să fie refăcute înrolările/reînnoirile în platformele instituțiilor unde vei folosi nou certificat, precum: ANAF, CNAS, UNNPR etc.
Verifică ce soluție există dacă ești într-una dintre cele mai frecvente situații ce pot genera erori la obținerea documentului de confirmare.
Reamintim, documentul se obține simplu și rapid din platforma de confirmare certSIGN. Oricând și de câte ori este necesar. Ai nevoie doar de certificatul tău digital calificat pentru semnătură electronică.
SOLUȚIE: Închide browserul și aplicația paperLESS vTOKEN și reia procedura. Redeschide aplicația paperLESS vTOKEN, apoi deschide platforma de confirmare și alege Autentificare cu certificatul. Codul de autorizare trebuie introdus cât mai rapid. Codul este generat de aplicația de autorizare instalată pe telefon.
SOLUȚIE: Documentul de confirmare precompletat este salvat automat în folderul destinat descărcărilor de pe calculator. Deschide documentul din folderul unde a fost salvat. Folosește doar aplicația Adobe Reader.
SOLUȚIE: Fișierul descărcat are denumirea prenume_nume.pdf (exemplu: mihai_ionescu.pdf). Caută în calculator un fișier cu acest nume.
SOLUȚIE: Reia procedura și urmărește cu atenție toți pașii din platformă. După ce ai semnat documentul, acesta trebuie încărcat din nou în platformă pentru a fi contrasemnat automat de certSIGN. După semnare vei primi mesajul “Descarcă documentul procesat”. Deschide documentul procesat doar cu aplicația Adobe Reader.
SOLUȚIE: Documentul de confirmare procesat (contrasemnat) este salvat automat în folderul destinat descărcărilor de pe calculator sub denumirea confirmare.pdf. Caută în calculator un fișier cu acest nume.
SOLUȚIE: Reia procedura fără sa faci nicio modificare a informaților din documentul precompletat. Documentul conține exact datele certificatului digital certSIGN cu care ești autentificat în platforma de confirmare. Informațiile sunt verificate automat și nu sunt acceptate modificări.
SOLUȚIE: Reia descărcarea documentului contrasemnat de certSIGN și nu îl modifica după descărcare. ANAF acceptă documentul doar dacă NU a fost modificat în niciun fel, iar salvarea sa este considerată o modificare.
SOLUȚIE: Reia procedura, începând cu autentificarea cu certificatul digital în platforma de confirmare certSIGN, și parcurge din nou pașii până la obținerea documentului de confirmare contrasemnat automat de certSIGN.
Achiziția Kit-ului certSIGN pentru semnătură electronică din catalogul SICAP se poate face parcurgând, în această ordine, etapele:
Dacă titularul nu se poate prezenta personal la un partener certSIGN, documentele pot fi trimise prin curier/postă la sediul central certSIGN, Documentele trebuie să fie însoțite de „Declarația pe proprie răspundere” autentificată notarial sau atestată de un avocat.
Adresa sedului central certSIGN: Bulevardul Tudor Vladimirescu, nr. 29A, Sector 5, București, clădirea AFI TECH PARK 1, etaj 2.
Factura fiscală va fi transmisă după emiterea certificatului și va avea 30 zile termen de plată.
În catalogul SICAP, produsele se găsesc astfel:
Achiziția certificatului certSIGN în CLOUD pentru semnătură electronică din catalogul SICAP se poate face parcurgând, în această ordine, etapele:
Dacă titularul nu se poate prezenta personal la un partener certSIGN, documentele pot fi trimise prin curier/postă la sediul central certSIGN, Documentele trebuie să fie însoțite de „Declarația pe proprie răspundere” autentificată notarial sau atestată de un avocat.
Adresa sedului central certSIGN: Bulevardul Tudor Vladimirescu, nr. 29A, Sector 5, București, clădirea AFI TECH PARK 1, etaj 2.
Certificatul digital se va emite automat la prima introducere a unui cod de autorizare, după autentificarea în contul din platforma cloud paperLESS webSIGN.
Factura fiscală va fi transmisă după emiterea certificatului și va avea 30 zile termen de plată.
În catalogul SICAP, produsele se găsesc astfel:
Semnătura electronică se realizează cu ajutorul certificatului digital calificat stocat pe TOKEN și, pentru utilizarea certificatului trebuie, mai întâi, instalată pe calculator aplicația de management a tokenului.
Așadar, dacă este prima utilizare a TOKEN-ului pe acest calculator:
Codul PIN este transmis folosind una dintre aceste două variante:
SAU
AI BLOCAT TOKEN-UL?
Pentru deblocarea TOKEN-ului și stabilirea unui nou cod PIN este nevoie de codul PUK. Codul PUK are 14 caractere și se găsește pe:
Reamintim: După primirea Kitului de semnătură, titularul a accesat un link primit pe email și, în pagina deschisă, a introdus informațiile solicitate și codul pentru generare primit de la certSIGN în plicul conținând Kitul de semnătură. Apoi a fost generat PIN/PUK.
SAU
Pregătește codul PUK și accesează secțiunea Deblocare token din pagina de Suport a website-ului certSIGN. Urmează pașii descriși ținând cont de modelul TOKEN-ului și de sistemul de operare* al PC-ului/laptopului.
*Sistemele de operare macOS Sonoma, Ventura și Monterey acceptă doar parole PIN de maxim 8 caractere.
Dacă NU mai sunt disponibile încercări de utilizare a codului PUK înseamnă că acest cod este blocat și nu se mai poate defini alt PIN. În această situație:
ALTE INFORMAȚII
Identificarea video neasistată este un element important în procesul de obținere a certificatului digital calificat pentru semnătură electronică. Emiterea este posibila doar după identificarea titularului de certificat digital calificat, în baza actului de identitate.
După încheiere, sesiunea de identificare video trebuie validata de certSIGN. Răspunsul nostru va fi transmis în maxim 24 de ore, pe e-mail. Dacă sesiunea:
Urmărește acest video care prezinta condițiile ce trebuie respectate în timpul identificării video.
Reamintim că, pentru realizarea identificării video, sunt necesare:
* Lista cu documentele de identitate acceptate la identificarea video este disponibila AICI.
În acest domeniu, certSIGN furnizează servicii precum:
Produse şi servicii
Cercetare și inovare
Citește mai multe detalii sau transmite-ne un mesaj.
În domeniul arhivării, certSIGN oferă servicii precum: prelucrare arhivistică, digitizarea documentelor, restaurare, depozitarea documentelor, eliberarea de adeverințe, lucrări de selecționare, distrugerea confidențială a informațiilor, procesarea şi stocarea documentelor electronice.
Sunt disponibile:
Serviciile și soluțiile certSIGN de securitate cibernetică acoperă toate scenariile pentru protejarea asset-urilor digitale în fața amenințărilor cibernetice, în concordanță cu reglementările legislative în vigoare și cu bunele practici din domeniu.
Află detalii despre:
Detalii legate de modalitatea de personalizare semnăturii astfel încât în aspectul acesteia să fie incluse și informațiile solicitate de OUG 140/2020 cu privire la specialiștii din domeniile construcții, arhitectură și urbanism sunt disponibile pe pagina Creare aspect semnătură OUG 140/2020
De asemenea, alte informații legate de semnătura electronică sunt disponibile pe pagina cu
Răspunsurile pentru cele mai frecvente întrebări ale clienților
Pentru a achiziționa de la certSIGN un certificat calificat pentru semnarea electronică a documentelor din domeniile construcții, arhitectură și urbanism, în conformitate cu OUG 140, trebuie urmate aceste etape:
Dacă informațiile legate de titularul certificatului sunt corecte și complete, certSIGN va expedia plicul cu Kit-ul pentru semnătură electronică la adresa poștală completată în cererea de înregistrare. Plicul va conține:
Codurile PIN/ PUK sunt generate electronic utilizând un mecanism automatizat: titularul primește pe e-mail un link. Accesează link-ul și, în pagina deschisă, completează codul pentru generare primit în plic și informațiile solicitate. Fișierul PIN.pdf rezultat trebuie salvat sau tipărit. Va fi necesar pentru următoarele utilizări ale TOKEN-ului.
Pentru acces în Sistemul Informatic Integrat Vamal (SIIV) la secțiunile AES și NCTS5 RO UMG Trader Producție trebuie să încarci certificatul tău calificat și certificatul intermediar al autorității care a emis certificatul. Certificatele se încarcă în platforma UMG Trader, într-unul dintre formatele .cer/.der/.crt.
CUM OBȚII CERTIFICATUL INTERMEDIAR ÎN FORMATUL SOLICITAT?
CUM OBȚII CERTIFICATUL PERSONAL ÎN FORMATUL SOLICITAT?
Pe pagina web Utilizarea certificatului de semnătură electronică în platforma Sistemul Informatic Integrat Vamal sunt disponibile mai multe detalii despre descărcarea certificatului titularului și a certificatului autorității intermediare solicitate la înregistrarea pentru depunerea declarațiilor vamale folosind semnătura electronică.
Dacă sesiunea de identificare video a fost întreruptă, din orice motiv, sau nu a putut fi validată, certSIGN va transmite pe email, în maxim 24 de ore, indicațiile necesare pentru reluarea și/ sau finalizarea procesului de identificare. Nu va fi necesară și reluarea plății. Condițiile care trebuie respectate pentru identificare sunt aceleași.
Așteaptă primirea noului link pentru identificare video și apoi reia procedura. Acordă atenție sporită condițiilor care trebuie respectate în timpul identificării.
Urmărește acest video care prezinta condițiile ce trebuie respectate în timpul identificării video.
Reamintim că, pentru realizarea identificării video, sunt necesare:
* Lista cu documentele de identitate acceptate la identificarea video este disponibila AICI.
După încheiere, sesiunea de identificare video trebuie validata de certSIGN. Răspunsul nostru va fi transmis în maxim 24 de ore, pe e-mail. Dacă sesiunea:
Pentru utilizarea certificatului certSIGN pentru semnătură electronică în platforma Spațiul Privat Virtual (SPV), recomandăm urmarea instrucțiunilor furnizate de ANAF pentru înregistrarea în SPV.
Pentru acces în Spațiul Privat Virtual (SPV), certificatul calificat emis de certSIGN trebuie înregistrat la SPV prin completarea informațiilor solicitate în platforma ANAF-SPV și încărcarea actelor solicitate, inclusiv documentul de confirmare contrasemnat de certSIGN la adresa: https://www.anaf.ro/InregPersFizicePublic/#tabs-2.
Pentru obținerea documentului de confirmare, urmărește unul dintre aceste tutoriale, în funcție de tipul de semnătură pe care îl ai:
NU AI GĂSIT CODUL PIN/PUK?
certSIGN transmite codurile PIN/PUK pentru certificatele pe TOKEN, folosind una dintre cele două variante:
CUM SE TRANSMIT PIN/PUK?
ELECTRONIC dacă adresa de email asociată certificatului digital a fost validată după completarea cererii de achiziție a certificatului.
Documentul conținând PIN/PUK trebuie generat electronic de titularul certificatului. Acest document se poate obține doar după primirea codului pentru generare. Se va accesa link-ul transmis de certSIGN pe email și, în pagina deschisă, se vor completa informațiile solicitate și codul pentru generare.
ATENȚIE: După 3 încercări nereușite de generare a PIN/PUK se blochează link-ul. Această situație trebuie semnalată către certSIGN.
După finalizare, documentul (PIN.pdf) conținând PIN/PUK trebuie salvat și păstrat în siguranță.
SAU
FZIC – document securizat, în plic, transmis prin curier la adresa poștală declarată la momentul achiziției, dacă adresa de email asociată certificatului digital calificat pentru semnătura electronică NU a fost validată după completarea cererii de achiziție a certificatului.
CUM OBȚII DOCUMENTUL DE CONFIRMARE?
Documentul de confirmare se obține simplu și rapid din platforma de confirmare certSIGN. Oricând și de câte ori este necesar. Ai nevoie doar de certificatul tău digital calificat pentru semnătură electronică.
Descarci documentul precompletat cu datele tale. Îl semnezi electronic. Transmiți documentul semnat pentru a fi contrasemnat automat de certSIGN. Primești documentul de confirmare semnat de certSIGN. Toate acțiunile în aceeași platformă.
Detaliat, pentru obținerea documentului de confirmare trebuie să parcurgi următoarele etape, în această ordine:
Urmărește unul dintre aceste tutoriale, în funcție de tipul de semnătură pe care îl ai:
Cum obții semnătura electronică în CLOUD?
Semnătura electronică se realizează cu ajutorul unui certificat digital calificat, iar pentru obținerea certificatului în CLOUD trebuie parcurse etapele:
Dacă informațiile legate de titularul certificatului sunt corecte și complete, certSIGN va trimite către adresa de email indicată în formularul de înregistrare două invitații:
Dreptul de utilizare al semnăturii electronice în cloud va fi acordat doar după configurarea mecanismului de autorizare și activarea contului de utilizator în platforma de semnare paperLESS webSIGN, conform instrucțiunilor primite.
Certificatul digital se emite automat, după autentificarea în contul din platforma de cloud webSIGN, la prima introducere a unui cod de autorizare.
Cum obții semnătura electronică cu TOKEN?
Semnătura electronică se realizează cu ajutorul unui certificat digital calificat, și pentru obținerea certificatului pe TOKEN trebuie parcurse etapele:
Dacă informațiile legate de titularul certificatului sunt corecte și complete, certSIGN va expedia plicul cu Kit-ul pentru semnătură electronică la adresa poștală indicată în formularul de înregistrare. Plicul va conține:
Codurile PIN/ PUK vor fi livrate independent de plicul ce conține TOKEN-ul. Livrarea documentului ce conține codurile se poate face:
Pentru mai multe informații poți vizita și pagina Semnătură electronică cu token.
Nu ai găsit ce căutai? Descrie cât mai detaliat situația pentru care ai nevoie de un răspuns.